You see that little padlock next to a website address and assume everything’s safe. But do you know what’s actually happening behind the scenes to secure that connection?
Most people don’t—and that’s the problem. Digital security feels invisible until it fails. What few realize is that each “secure” session starts with a complex set of behind-the-scenes protocols—specifically, the signal handshake protocols—that quietly verify identity and encrypt your data before a single page loads.
This article is your no-nonsense walkthrough of what really happens when your browser says it’s safe. We’ll break down how devices say “hello,” establish trust, and build an encrypted tunnel that protects your most sensitive online actions.
We’ve spent years unpacking the bedrock of encryption and digital communication. This isn’t surface-level tech talk—we’re here to strip away the jargon and show you, step by step, how secure connections begin, function, and protect your privacy.
By the end, the lock icon won’t just look safe—you’ll know why it is.
The Foundation: What is a Communication Protocol?
At its core, a communication protocol is a set of rules that devices follow to exchange data—think of it as a shared digital language. Without these protocols, your devices wouldn’t know how to talk to each other (kind of like trying to play chess without knowing the rules).
But not all protocols are built the same. Standard ones like HTTP and FTP may be familiar, but they come with a glaring flaw: they transmit everything in plain text. That’s a problem when sensitive data is involved. In 2022 alone, over 22 billion records were exposed globally due to unencrypted transmissions (source: RiskBased Security).
That’s where secure communication protocols come in, focusing on three pillars:
- Confidentiality—using encryption to shield your data
- Integrity—ensuring the message arrives unaltered
- Authentication—verifying who you’re really talking to
A strong example is signal handshake protocols, which ensure those principles are upheld in real-world messaging apps. When WhatsApp adopted this protocol, it secured communications for 2+ billion users globally.
Pro tip: If your app doesn’t support encryption by default, it’s not secure—no matter how sleek the interface looks.
The Main Event: TLS and The Digital Handshake
Here’s my take: If the internet were a massive networking event, TLS is the polished, security-savvy bouncer at the door, checking IDs, verifying credentials, and making sure the conversation inside stays private.
Transport Layer Security (TLS) has become the gold standard for securing connections between devices on the web. It’s what keeps your data encrypted and away from eavesdroppers. Its predecessor, SSL, held the role for years but has since been retired—think of it as the analog flip phone in a smartphone era. (Nostalgic? Sure. Secure? Not anymore.)
And now, the actual exchange—the so-called digital handshake. Here’s where things get really interesting.
The Handshake Process – Step-by-Step
-
Client Hello
The process kicks off when your browser sends a friendly wave—technically known as the Client Hello. This message includes the version of TLS it’s using and a list of cipher suites (just fancy names for encryption formulas) it’s cool with. -
Server Hello
The server responds with a Server Hello. It finalizes the TLS version, picks a cipher suite to use (ideally one both sides like), and hands over a digital certificate—basically its online passport. -
Certificate Verification
Here’s the pro move: your browser actually checks that certificate with a Certificate Authority (CA)—a trusted third party in the online world. If it passes, your browser green-lights the connection. (If it doesn’t? Expect a big scary warning screen.) -
Key Exchange
This is where the real magic happens. A secure key exchange takes place—both sides create and agree on session keys to encrypt data for the duration of the connection. No one else is invited to this party. Think of it as digital whispering.
Pro Tip: When set up correctly, TLS combined with signal handshake protocols is nearly bulletproof for secure communication—even if you’re sipping café Wi-Fi (just make sure it’s HTTPS, not HTTP, okay?).
Securing modern connections isn’t just important—it’s fundamental. And TLS? It’s the silent hero making sure you don’t have to think twice before clicking “submit.”
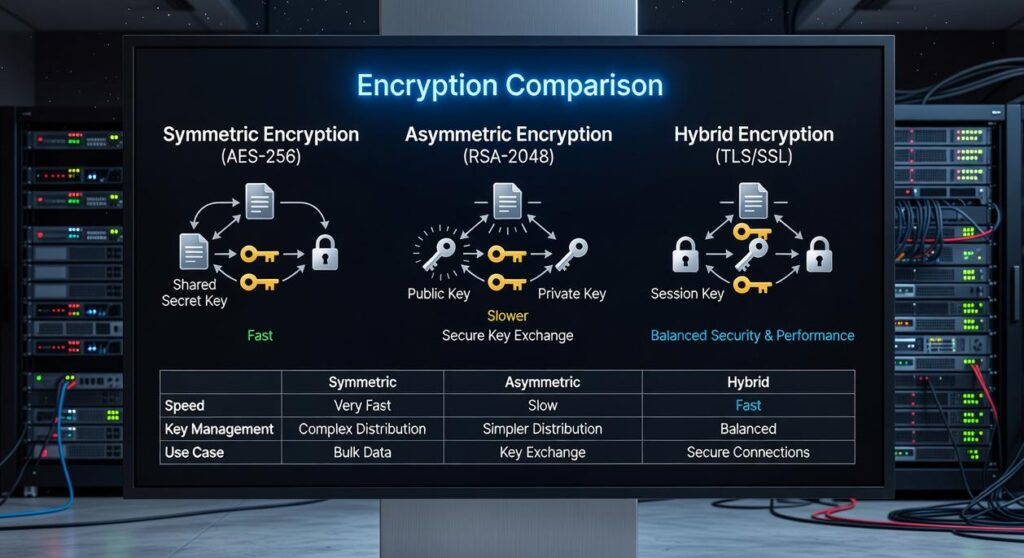
The Secret Ingredient: Asymmetric vs. Symmetric Encryption

Let’s clear something up right away: encryption isn’t one-size-fits-all. Two main styles—asymmetric and symmetric encryption—work together like a buddy-cop duo. One’s slow and secure, the other’s fast and efficient. Here’s how they split the workload.
Asymmetric encryption, also known as public-key encryption, kicks things off. During the signal handshake protocols, your device and a server exchange cryptographic greetings (cue spy music). The server shares its public key, which your device uses to lock up a one-time-use session key. Only the server’s private key can unlock it. It’s a safe move, because intercepting the public key won’t help an attacker—without the private key, they’re just holding a fancy paperweight. Downside? It’s slow. (Imagine mailing a locked box back and forth every time you want to say hi.)
That’s where symmetric encryption takes over. Once both parties have the same session key, they use it to encrypt and decrypt messages quickly. Think of it as switching from a lockbox to a walkie-talkie—much faster.
That’s the secret sauce of secure web connections: we kick things off with secure-but-slow asymmetric encryption, just to hand things off to fast-and-safe symmetric encryption.
Pro tip: This dance of encrypted hellos and secure speed is exactly how TLS (the protocol behind HTTPS) keeps your web browsing private.
For more on encryption in everyday tech, check out the top 5 encryption algorithms used in modern communication.
Beyond the Browser: Other Key Secure Protocols
We get it—everyone obsesses over HTTPS like it’s the only kid at the encryption party. But what about the rest of the crew working behind the scenes? Here’s the frustrating truth: while HTTPS secures your browser, tons of sensitive work happens outside the browser. So why do we act like the risks vanish once we log out of Chrome?
Take SSH (Secure Shell), for example. If you’ve ever had to access a server remotely, you know the pain of relying on clunky or insecure methods. SSH steps in as the superhero here, offering encrypted command-line access—absolutely essential for sysadmins managing machines around the globe. Yet too many still use unprotected protocols (cue the collective IT scream).
Then there’s SFTP, the secure sibling of FTP. It runs on an SSH backbone, encrypting all file transfers. Old-school FTP sends your data naked across the web (seriously), but SFTP ensures your files aren’t easy bait for cyber snoops.
And let’s talk VPN protocols like OpenVPN and WireGuard. These create encrypted tunnels for all your traffic—not just a browser tab. Think of them as your device’s invisibility cloak. Setup can be tedious, sure (cue: signal handshake protocols), but it’s worth it to protect against prying eyes on public Wi-Fi.
Pro tip: If you’re not using these tools yet, you’re not as invisible online as you think.
From Handshake to Secure Conversation
You came here wondering what that tiny padlock in your browser really means—and now you know.
Behind every secure website visit lies a carefully orchestrated dance of protocols that authenticate, encrypt, and verify. Specifically, signal handshake protocols like TLS ensure that your data is protected from prying eyes while confirming you’re communicating with the real source.
We’ve broken down the mystery for you: multi-step verification, certificate checks, and two-layer encryption working invisibly in the background. This interplay of trust and privacy is no longer a black box—it’s a powerful safeguard you now understand.
Security isn’t automatic—it’s built, verified, and constantly updated.
Here’s what to do next: The next time a browser warning pops up about an unverified certificate or insecure page, don’t ignore it. That’s your signal something might be wrong.
These protocols are your silent defenders—and staying alert is your new advantage.