You’re probably here because you’re trying to figure out which encryption method—aes vs rsa—makes the most sense for your system. If you’ve ever wondered whether your current choice is slowing you down or leaving your data exposed, you’re not alone. Getting this wrong can mean more than just inefficiency—it can mean vulnerability.
This guide clears up the confusion. We’re breaking down aes vs rsa in plain terms: how they work, where they shine, where they don’t, and exactly when to use each. No guesswork—just direct answers.
We specialize in translating complex encryption concepts into clear, real-world decision points. You can trust that what you’re getting here is accurate, current, and tailored to help you make smarter security choices.
By the end of this article, you’ll know the strengths, weaknesses, and ideal use cases for both algorithms—so you can choose the right shield for your data.
Understanding AES: The Symmetric Workhorse
You’ve probably heard about AES. But what exactly makes it the go-to encryption tool in the digital world?
AES—short for Advanced Encryption Standard—is a symmetric-key algorithm. That means the same secret key is used to both scramble and unscramble your data (handy, but also why keeping that key protected is everything).
Here’s how it works: AES is a block cipher, meaning it slices your data into 128-bit chunks and processes each block through a series of algorithmic twists. It supports key lengths of 128, 192, or 256 bits—the longer the key, the tougher it is to crack (and yes, government-level secure).
The real ace up AES’s sleeve? Speed. It’s designed to be lightning-fast, making it the global standard for encrypting massive data—whether stored on your hard drive or speeding across the internet.
Still wondering about aes vs rsa? Fair question. RSA is asymmetric and better for key exchanges, while AES shines when raw speed and high-volume security are required.
Looking ahead: Want to know how AES fits into VPNs, password managers, or your smartphone’s encryption? That’s what we’ll explore next.
Understanding RSA: The Asymmetric Gatekeeper
RSA (short for Rivest-Shamir-Adleman) is one of the foundational building blocks of modern encryption. It’s an asymmetric-key algorithm, meaning it uses two different keys instead of one: a public key to encrypt and a private key to decrypt. (Think of it like giving everyone a locked mailbox, but only you have the key to open what’s inside.)
How RSA Works—and Why That Matters
Here’s why RSA caught fire: it solves the age-old problem of secure key exchange. In symmetric encryption, both parties need the same secret key, which leads to the risky business of sharing that key securely in the first place. But with RSA, anyone can encrypt a message using your public key—only your private key can decrypt it. Instant security, no awkward handshakes.
Its real strength? Digital signatures. RSA lets you verify identity with mathematical certainty—crucial in everything from email verification to cryptocurrency wallets.
Speculation ahead: Although RSA remains rock-solid for now, post-quantum updates may challenge its reign. More agile, quantum-resistant algorithms are gaining attention—especially in the ongoing aes vs rsa debate, where symmetric algorithms may offer faster, future-proof alternatives. Just don’t count RSA out yet. The encryption gatekeeper isn’t stepping down anytime soon.
Head-to-Head Comparison: AES vs. RSA
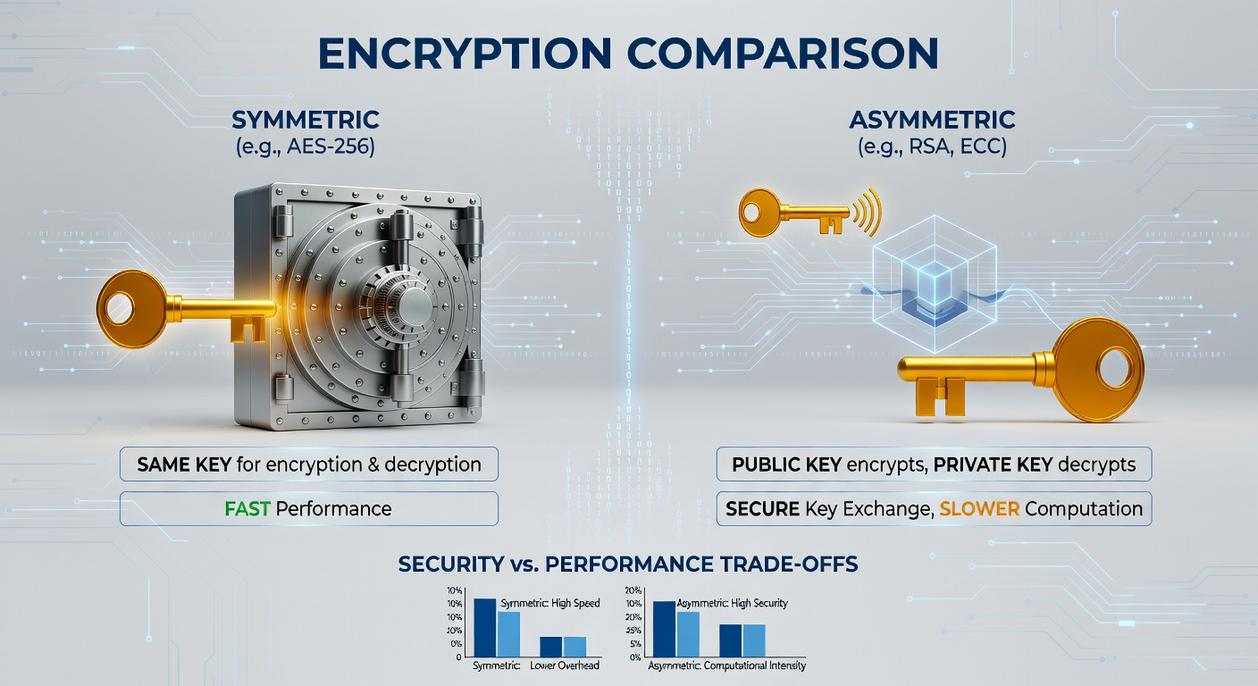
Key Type & Management
When it comes to key management, the contrast is pretty stark. AES (Advanced Encryption Standard) uses a single symmetric key — both the sender and receiver need access to the exact same secret key. And there’s your snag: securely getting that key to both ends without someone eavesdropping? Not trivial. (Think of it like mailing your house key and hoping it doesn’t get lost or copied on the way.)
RSA, on the other hand, uses an asymmetric approach — a public key anyone can access, and a private key only you hold. Personally, I find this public-private setup elegant. It solves the key distribution headache and opens the door to digital signatures and secure key exchanges. If you ask me, that’s a major win in real-world deployment.
Speed and Performance
Let’s not mince words: AES is fast. It’s designed to be — block cipher operations optimized for performance, especially when hardware acceleration comes into play (hello, AES-NI). Whether you’re encrypting huge files, streaming video, or securing a full-disk system, AES barely blinks.
RSA?, It’s the cryptographic version of a heavyweight boxer. Strong, sure, but not quick. RSA’s operations—especially decryption—are CPU-intensive due to the large key sizes and complex prime factoring math. In practice, you’d never use RSA to encrypt large volumes of data directly—it’s just not built for that. (Pro tip: Use RSA to encrypt the AES key, and let AES handle the payload.)
So in aes vs rsa, for performance-heavy applications, AES isn’t just better—it’s essential.
Security and Key Length
Security’s an arms race, and quantum computing has shown up to the party with new weapons. AES-256 is already considered quantum-resistant, and that’s not hype—NIST and NSA both endorse it for top-secret use.
RSA? Not so lucky. Its strength comes from the difficulty of factoring large numbers, something a quantum computer could theoretically tear through like a cheat code in a video game. Yes, increasing RSA key length helps (2048-bit is decent, 4096-bit is safer), but that only worsens its performance gap.
If you’re choosing between them for future-proof encryption, AES-256 is my clear choice.
Practical Use Cases: When to Use Which Algorithm
Have you ever wondered why your Wi-Fi is encrypted one way, but your online banking app uses a completely different method?
It all comes down to how much data you’re dealing with—and how quickly it needs to be secured.
When should you use AES? Think about encrypting your entire hard drive (like with FileVault or BitLocker), securing large databases, or protecting the traffic in VPN tunnels and Wi-Fi networks (WPA2, anyone?). AES, or Advanced Encryption Standard, shines when there’s a lot of data to lock down—fast and efficiently.
What about RSA? This one’s ideal when you need to verify identity or trust. It’s commonly used for digital signatures and securely exchanging keys. For instance, RSA helps send an AES key safely, so you can then use AES for the actual data encryption. (Smart, right?)
This combo is common in secure web protocols like TLS/SSL. RSA sets the secret handshake; AES handles the real work.
So in the aes vs rsa debate—why not both?
The Right Tool for the Right Security Job
If you’ve ever struggled with choosing between aes vs rsa, you’re not alone.
Many systems fall short because the wrong algorithm is used for the wrong task—slowing down performance or, worse, leaving data exposed.
Now you know it’s not about which is stronger overall—aes vs rsa is a question of function, not competition. Each shines in its own role. RSA handles key exchange with precision, while AES delivers speed and strength in encrypting bulk data.
That’s why top-performing systems don’t choose one—they combine both.
You came here looking for clarity. Now you know how these encryption methods work together to build efficient, secure systems.
Here’s what to do next: Audit your security architecture today. Make sure you’re not overloading RSA or under-utilizing AES. Back your infrastructure with a hybrid model that’s proven, smart, and secure.
This combo is the standard for a reason—and it’s the upgrade your system needs now.
